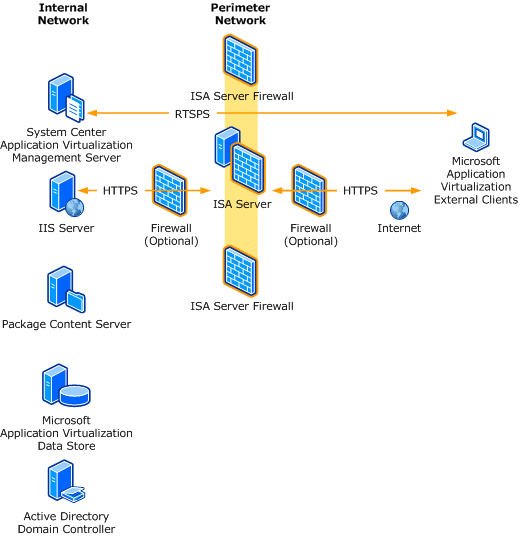
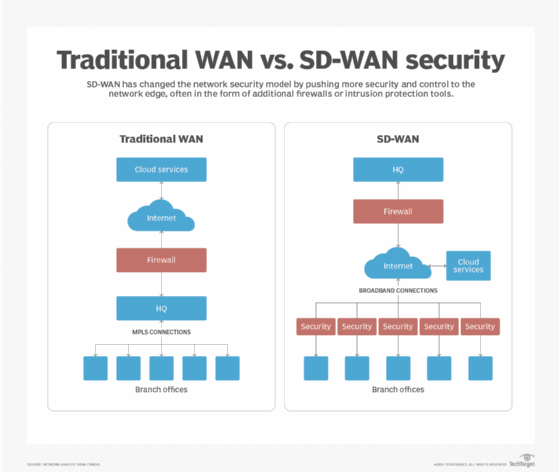
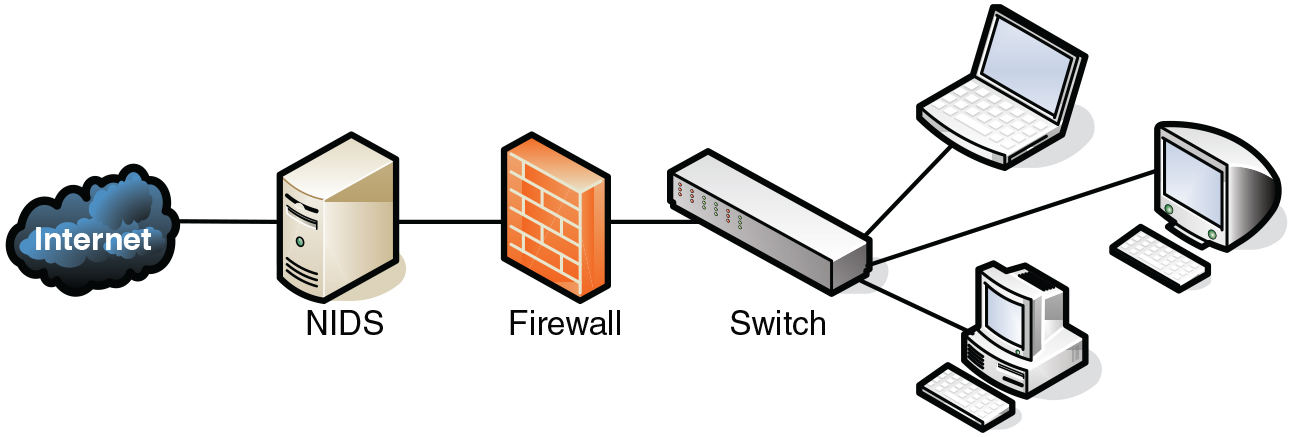
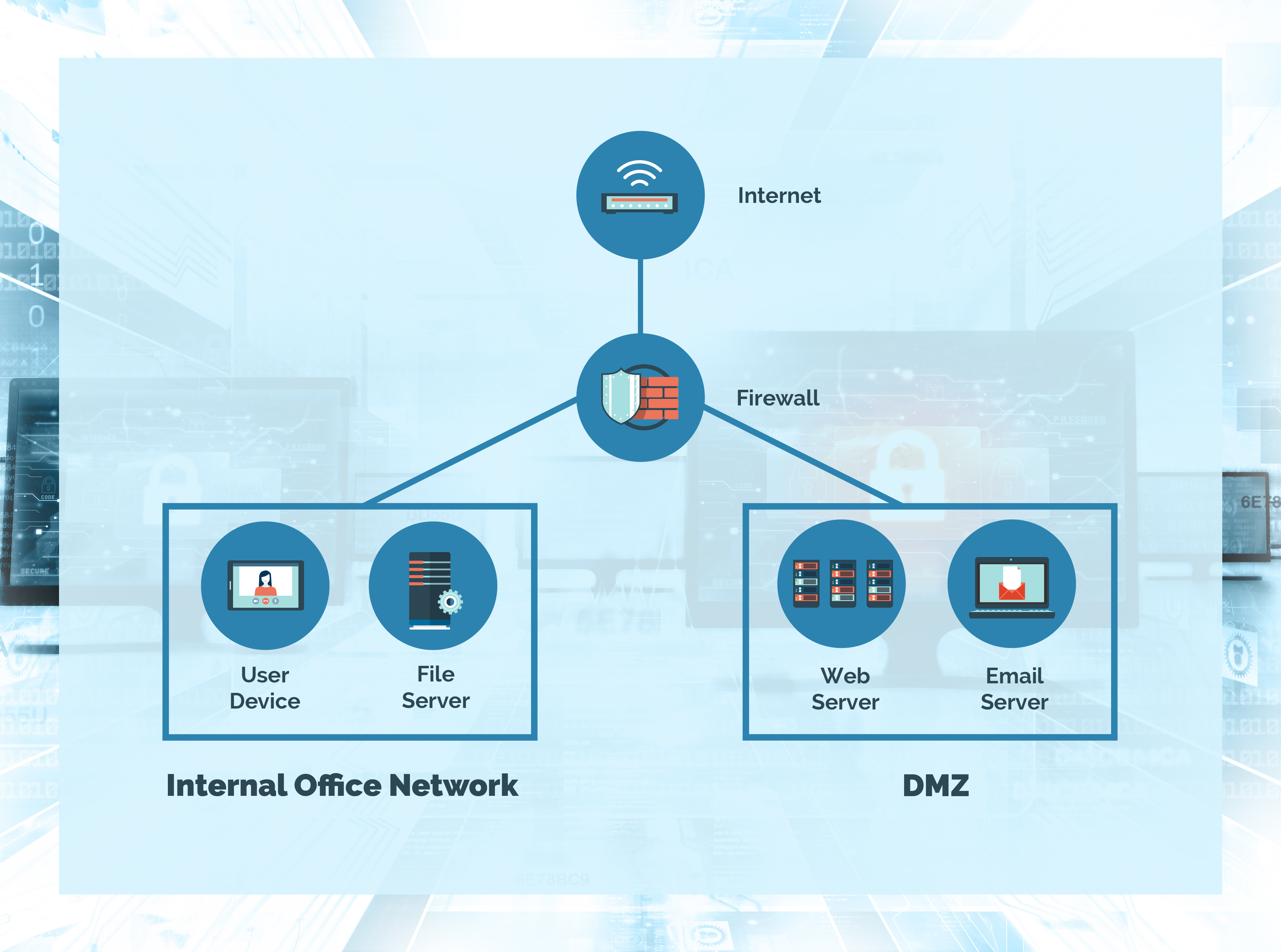
Network Configuration for Workgroup PDM Viewer in a Perimeter Network - 2012 - SOLIDWORKS Installation Help
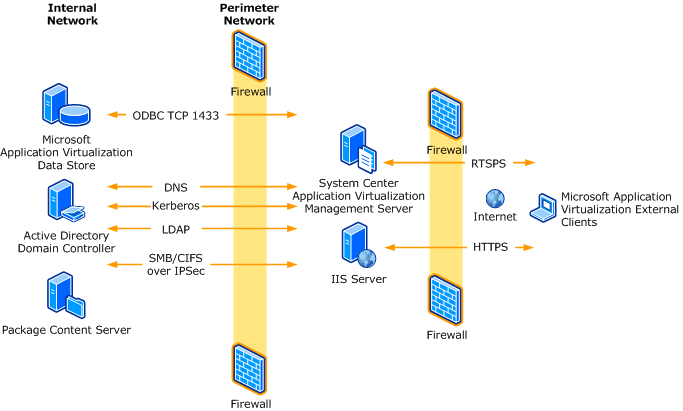
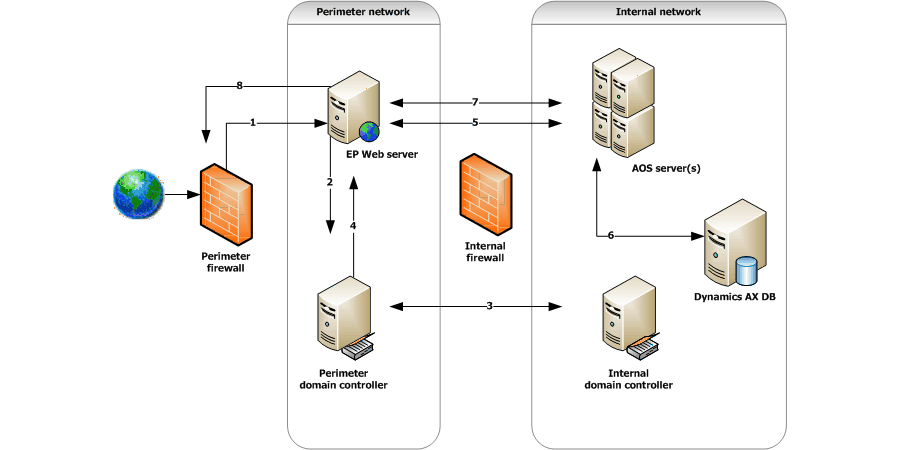
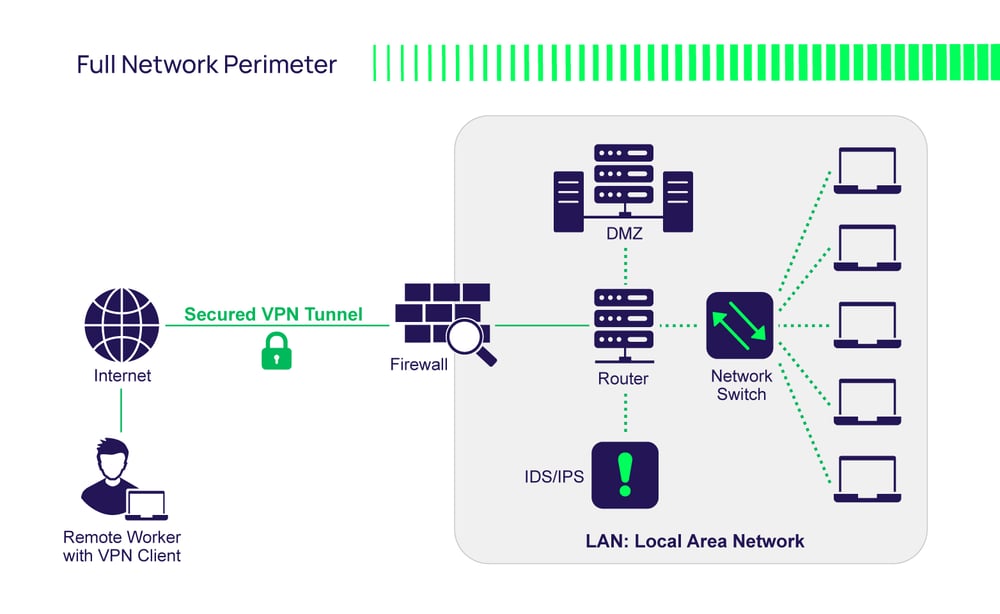
Internet-Facing Server Scenarios for Perimeter Networks - Microsoft Desktop Optimization Pack | Microsoft Learn
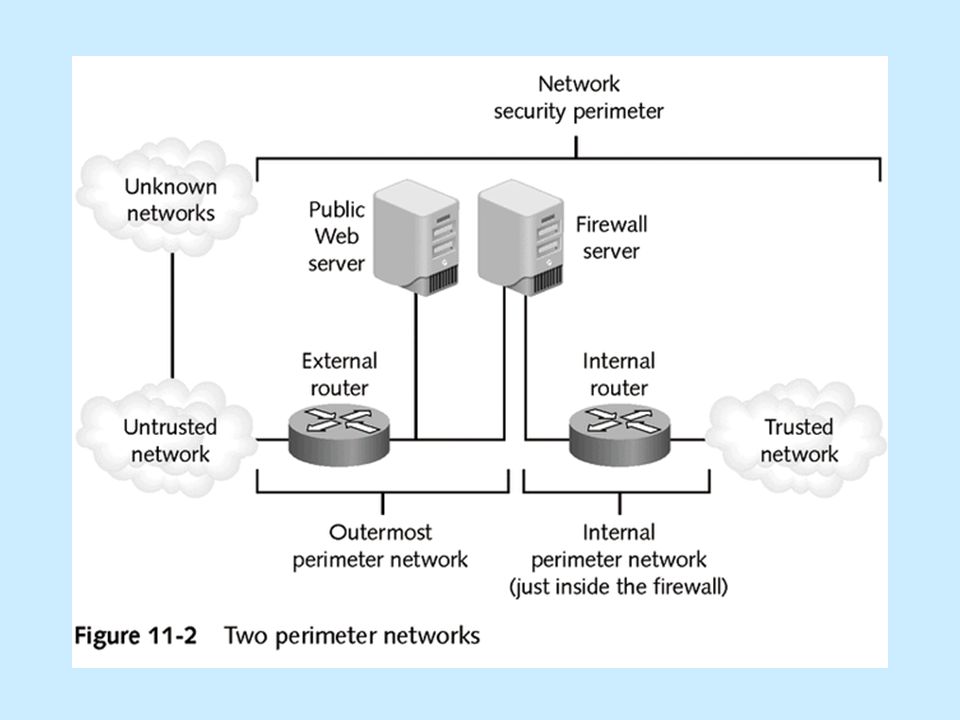
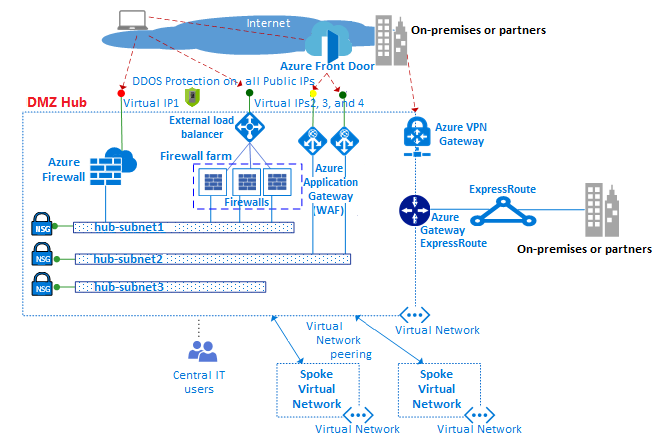
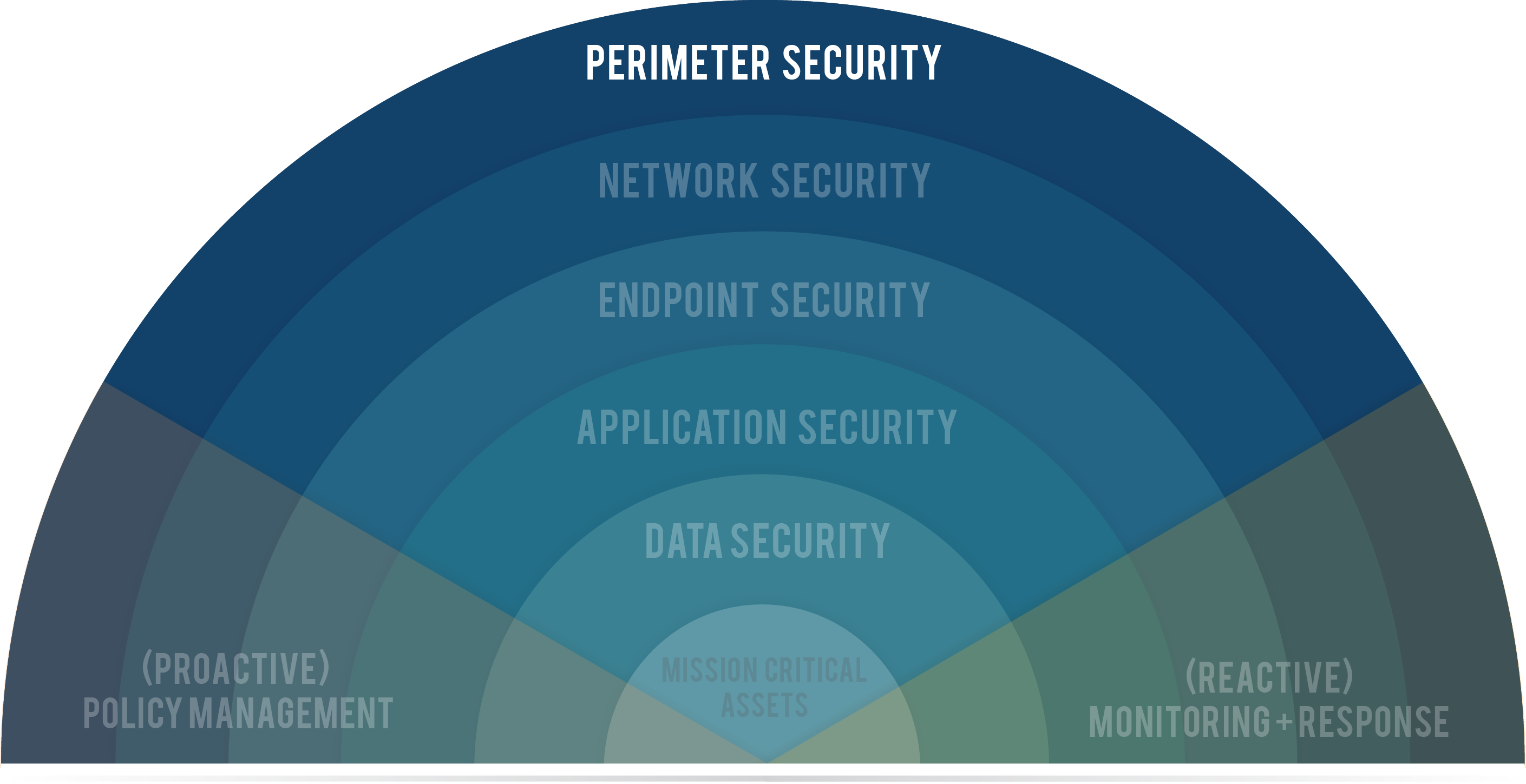
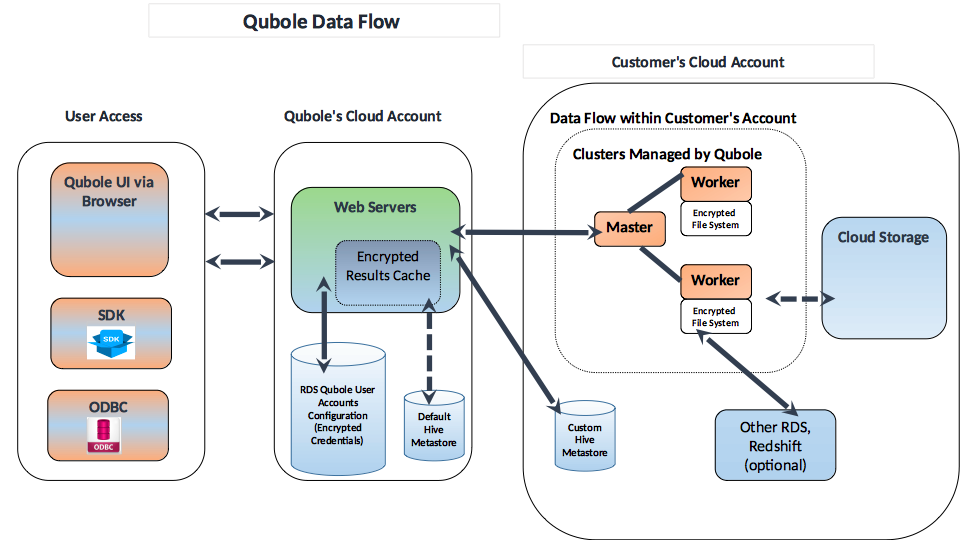
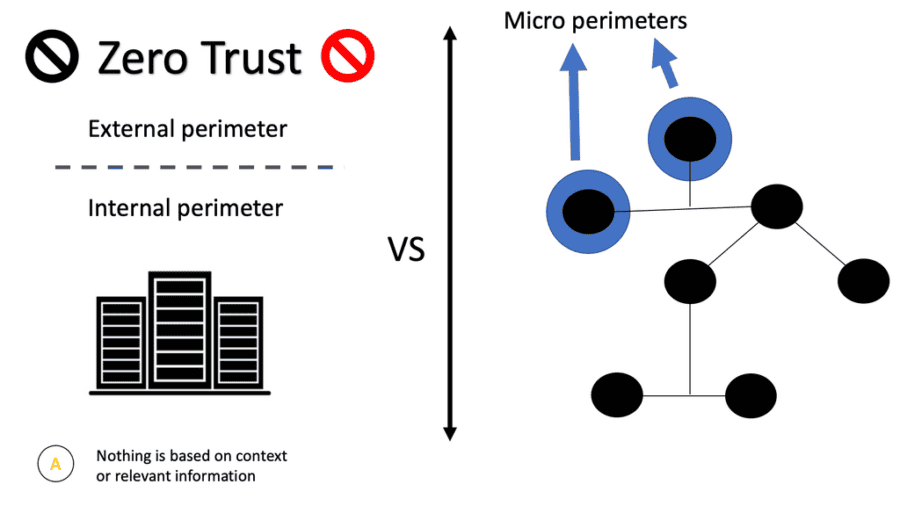
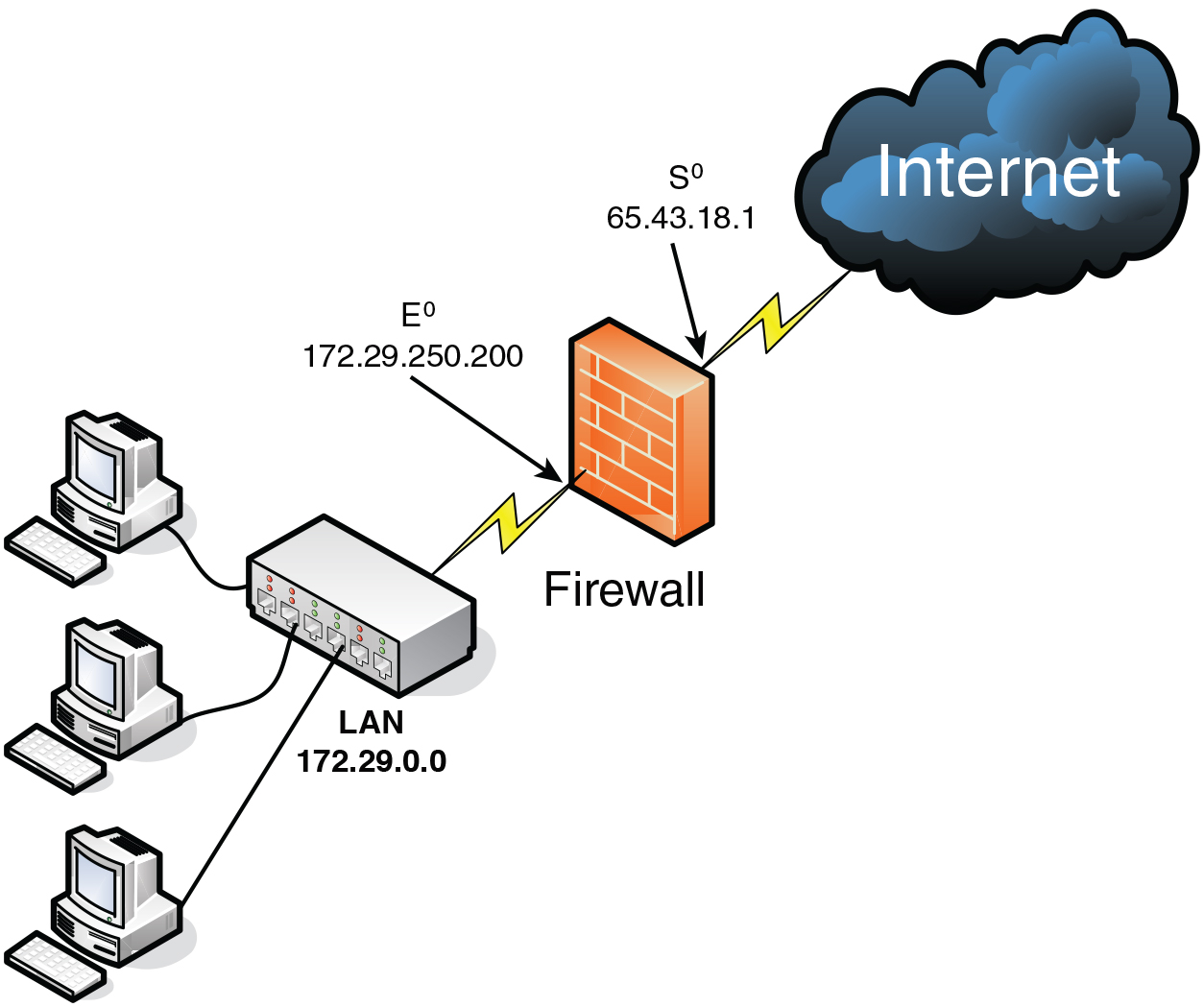
Network Security Topologies Chapter 11. Learning Objectives Explain network perimeter's importance to an organization's security policies Identify place. - ppt download